In today’s fast-moving world of software development, security must be woven into every phase of the process. This integration is what we call DevSecOps. It emphasizes the need to think about security throughout the development lifecycle, spotting and fixing vulnerabilities early and often. In this post, we will take a closer look at the DevSecOps lifecycle, examining its key stages, benefits, and best practices.
Understanding the DevSecOps Lifecycle
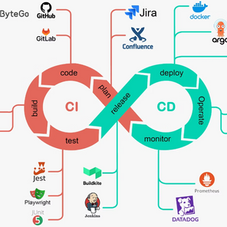
The DevSecOps lifecycle integrates security practices within the DevOps process, ensuring that security is a shared responsibility among all team members. It begins with planning, where security requirements are defined alongside development goals. Next, secure coding practices are implemented during the development phase. Continuous testing for vulnerabilities occurs throughout the integration and deployment stages. Finally, monitoring and feedback loops are established to maintain security post-deployment, adapting to new threats as they arise.
Benefits of Adopting the DevSecOps Lifecycle
Implementing DevSecOps lifecycle offers several advantages, improving both the development process and software quality.
Early Vulnerability Detection
Faster Time to Market
Increased Team Collaboration
Regulatory Compliance

Stages of DevSecOps Lifecycle
Stage | Description | Key Actions |
Plan | The starting point for all projects, where requirements and strategies are defined. |
|
Code | Developers write application code, and infrastructure engineers configure cloud resources. |
|
Build | Code is compiled, applications are packaged, and preparations for testing and deployment begin. |
|
Test | Applications undergo testing to identify and resolve bugs, vulnerabilities, and performance issues. |
|
Release | Applications approved and tested are prepared for deployment to various environments. |
|
Deploy | Applications are moved to production or target environments for real-world use. |
|
Operate | Applications are managed in production to ensure stability, availability, and performance. |
|
Monitor | Continuous tracking of application performance, security, and usage to detect and respond to issues. |
|
Detail Breakdown of Each Stages Of Lifecycle
Stage 1: Plan
The planning stage sets the groundwork for the DevSecOps lifecycle. It focuses on defining the project's goals and integrating security from the very start.
Here are key activities in the planning phase:
Requirement Gathering: It is critical to pinpoint both functional and security needs early. For instance, if you're building a financial application, understanding compliance requirements like PCI DSS is essential.
Risk Assessment: Identify potential risks that could affect the project. For example, if you are developing a health app, you should evaluate risks related to patient data breaches.
Engaging cross-functional teams during this phase builds a culture that values security. Developers, operations, and security professionals should collaborate to foster a shared sense of responsibility.
Stage 2: Develop
In the development phase, teams begin coding. Security should not take a backseat during this process.
Essential practices include:
Secure Coding Practices: Encourage adherence to standards like OWASP Top 10. For instance, developers should avoid common pitfalls such as SQL injection or cross-site scripting.
Automated Scanning: Utilize Static application security testing (SAST) tools. For example, tools like SonarQube can help identify code vulnerabilities early on, allowing teams to fix issues before they grow.
Regular code reviews and Dynamic application security testing (DAST) also play a role in strengthening security during this phase by complementing automated testing.
Stage 3: Build
The build stage is where the coded software gets compiled and packaged. Here, security considerations are just as important as speed.
Focus areas during this stage include:
Dependency Management: Use tools like Snyk to check open-source libraries for vulnerabilities. Statistics show that 70-80% of applications rely on open-source components, making this a critical step.
Continuous Integration: Integrate security testing within your CI/CD pipeline using tools like Github Action or Jenkins. This ensures security checks happen automatically, saving time and reducing risks.
This proactive approach enables teams to deliver software quickly while still managing security risks effectively.
Stage 4: Test
Testing reveals how secure the software is. This phase demands rigorous testing strategies that address both functionality and security compliance.
Consider the following during testing:
Dynamic Application Security Testing (DAST): Conduct real-time tests of running applications to catch vulnerabilities. For example, testing a web application’s payment process can uncover issues that static testing may miss.
Penetration Testing: Ethical hackers can simulate real-world attacks. A study showed that 90% of companies that engaged in penetration testing discovered vulnerabilities that went unnoticed by automated scans.
Including security experts in testing ensures that it is a priority, not an afterthought.
Stage 5: Release
The release phase transitions software from development to production, requiring diligent security practices to safeguard users.
Considerations during this stage include:
Change Management: Implement controls to stop unauthorized changes during deployment. This can reduce errors and security risks.
Security Reviews: Perform final security assessments using both automated scans and manual checks to verify compliance with established security practices.
By ensuring robust security evaluations before release, organizations can protect users from potential vulnerabilities.
Stage 6: Deploy
In the deployment phase, software moves into the live environment. Security still needs to be a top priority.
Key elements here include:
Infrastructure as Code (IaC): Using IaC allows teams to automate and secure processes, leading to scalable and repeatable deployments. Tools like Terraform can make infrastructure predictable and less prone to error.
Runtime Protection: Implementing runtime application self-protection (RASP) can help monitor applications in real-time. This can lead to a 50% reduction in successful attacks.
Embedding security into deployment creates a safer environment for both users and systems.
Stage 7: Operate
Once deployed, maintaining software is crucial. Security does not stop after deployment.
Important activities in this phase are:
Continuous Monitoring: Utilize tools to track logs and performance, allowing for quick detection of anomalies. For example, tools like Splunk can assist in spotting unusual user activity.
Incident Response: Develop a clear incident response plan. Statistics show that organizations with incident response plans are 50% faster in recovery from security breaches.
By maintaining a focus on security post-deployment, organizations protect software and users from emerging threats.
Stage 8: Feedback
Collecting feedback is vital for continuous improvement in the DevSecOps lifecycle. Understanding what works and what doesn’t is key to evolving security practices.
Effective feedback strategies include:
Post-Mortem Analysis: Conduct evaluations after incidents to identify weaknesses. This can strengthen security measures for future projects.
Metrics and Reporting: Setting KPIs (Key Performance Indicators) helps assess security performance. For instance, tracking the number of vulnerabilities found and fixed can guide improvements.
By refining processes based on real-life experiences, organizations can enhance both development and security.
Conclusion
In conclusion, the DevSecOps lifecycle is a comprehensive approach that integrates security into the software development process from planning to operation. By embedding security at every stage, organizations can proactively identify and mitigate risks, ensuring that security is not an afterthought but a fundamental aspect of development. This holistic integration fosters a culture of collaboration among development, security, and operations teams, ultimately leading to higher quality software and enhanced user protection.
As organizations continue to navigate the complexities of modern software development, embracing the DevSecOps lifecycle will be crucial for maintaining a competitive edge, ensuring compliance, and safeguarding against evolving threats. Continuous improvement through feedback and metrics will further strengthen security practices, making DevSecOps an indispensable framework for today’s digital landscape.